How To Hack A ComputerBefore discussing the methods of hacking a computer, we should know what Hacking is and is it a good approach to hack a system or a bad approach? What is HackingIn simple terms, Hacking is a process of getting illegal access to a device that may include a mobile phone, computer, networks, social media accounts, or other authorized accounts. For example, hacking the password of a computer and gaining access to it. Although it is an illegal process, it is not always performed for bad deeds. The person who does hacking is known as a Hacker. These people have complete or even depth knowledge about the devices. Therefore, if a device is not strongly secured, it becomes easy for hackers to break the security and enter the device and hack it. A Hacker is responsible for finding the weakness of a computer and gaining access over the system. There are different types of hackers where some are known as official hackers as they perform the illegal process for accomplishing a legal task. On the other hand, there are unofficial hackers who, with no official goal, hack a device illegally. Thus, hacking a computer or other device illegally is a crime for which the hacker can be arrested in an unlawful activity approach. There are various hacking techniques the What is Ethical HackingWe discussed about an official hacking and an unofficial hacking. The Hacking, which is performed for an official task, it is known as Ethical Hacking. If the Hacking is performed for an unofficial offense, it is known as a Cybercrime. Ethical Hacking is legal, but such ethical hackers abide by certain rules that should be followed while hacking a device. Here, we will discuss a method through which we can hack a computer. Hacking Method: Bypassing Login on the ComputerBypassing a login on a computer means to skip the login screen and directly enter the desktop of the computer. If we successfully did this for hacking a computer where we don't know the password of our prey's system, it means we successfully hacked the system. We will discuss the steps to bypass the password of a Windows 10 computer system. While doing so, one must know that the security features of Windows 10 do not permit us to deal and unauthenticate the Administrator account. Thus, we need to create a new administrator on the system which we are going to hack. Using this bypass method, one will not be able to change the password of the main administrator account but will be permitted to change the system settings virtually. Follow the below steps to bypass login on Windows 10: - You need a spare flash drive having at least 8GB storage and attach it to the CPU or laptop.
- Now, open Windows 10 installation drive on the computer. If not available, create one such partition.
- Open the 'Windows 10 download' page on your computer.
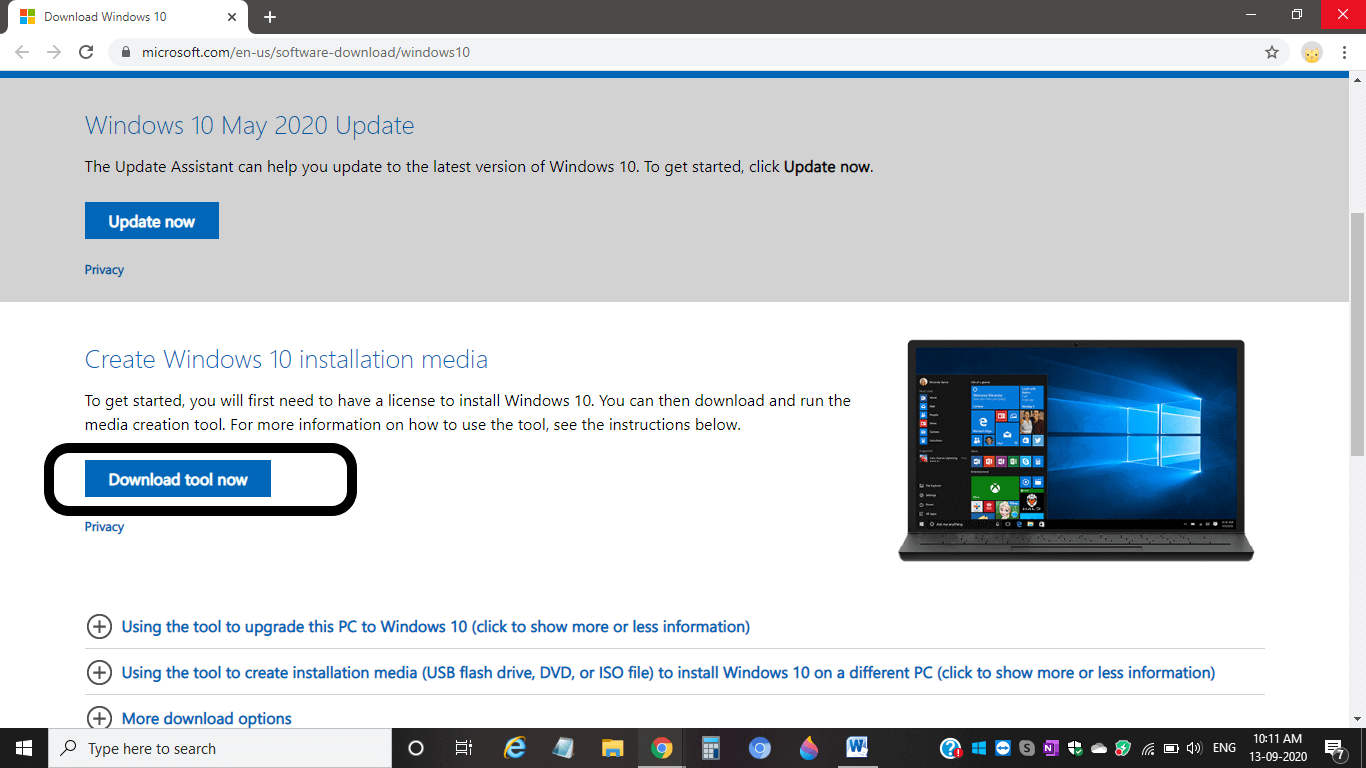 - Then click on the 'Download tool now'.
- After downloading the tool, double-click on it.
- Make sure the location chosen for installation is the flash drive.
- Do not remove the flash drive when the process gets completed.
- Now, we need to change the boot order of the computer as we need to restart our computer via the flash drive, instead of starting it via hard drive. For this, open Settings > Update & Security > Recovery.
- There we will see 'Advanced startup' with other available options. Click on 'Restart now' under it.
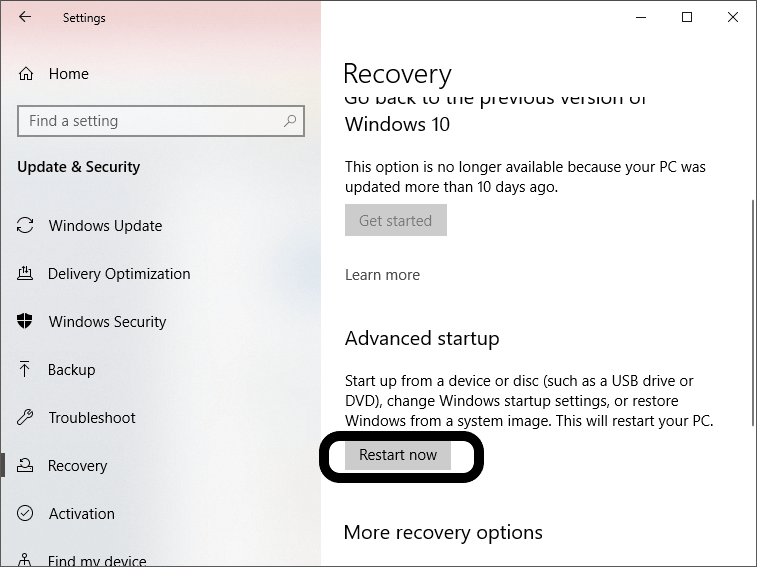 - Under the Boot option, select the name of the attached flash drive and press the up arrow key to make the flash drive reach the top.
- Save and exit from it.
- We will move to a setup screen, press Shift + F10 keys together on our computer, and the command prompt of our system will open.
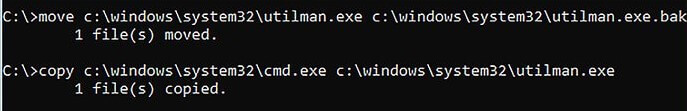
- Remove the utility manager with cmd so that we can easily execute the administrator-level functions and do not need to login to the computer. For doing so, type:
"move c : \ windows \ system32 \ utilman . exe c : \ windows \ system ' ' ' 32 \utilman . exe . bak" command in the command prompt. Then press enter.
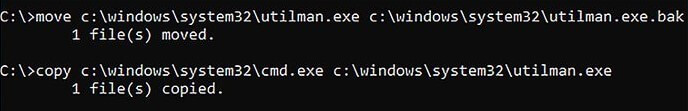 - Again type "copy c ; \ windows \system32 \ cmd . exe c : \windows \system32 \utilman . exe" command in the command prompt of the computer.
 - After replacing the utility manager, we need to restart the computer. To do so, type the' wpeutil reboot' command on the command prompt and press Enter. A snapshot is shown below:
 - While doing so, remove the flash drive or the installation media from the computer. It will ensure that the rebooting process begins to the login screen and not on the installation setup. However, if Windows reboots into the installation setup and still there is a chance to disconnect the installation media from the system, remove it without wasting a second. Then, press and hold the Power button of the laptop or CPU.
- Once the lock screen page loads successfully, click on the 'Utility Manager' icon present at the right bottom corner of the screen, as shown below:
 - The Command Prompt will open. However, if we didn't replace the Utility Manager with the 'Command Prompt' (as discussed in the above steps), it will open the 'Utility Manager' only. So, the command prompt will open, as shown below:
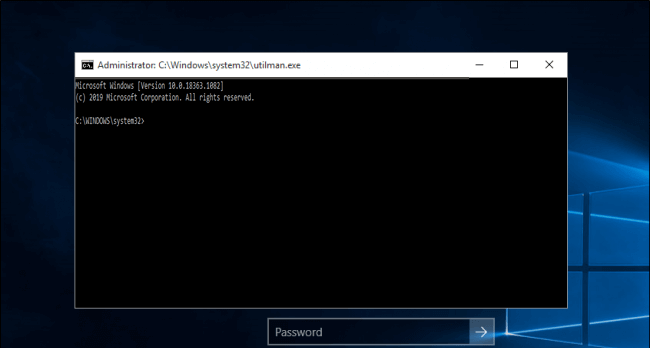 - Now, there is a need to create a new user so as to access the system privileges. To do so, type "net user <name> /add" command in the command prompt.
Press Enter. Again type "net localgroup administrators <name> / add" command in the cmd. Then press Enter. A snapshot is shown below:
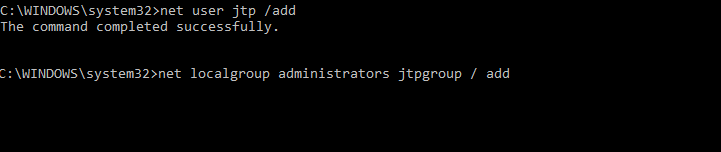
Note: The <name> value should be the same that we are creating as a user.- We need to restart the computer by clicking on 'Restart' under the Power icon present next to the 'Utility Manager' icon.
- When the system starts again, we will find our created account below the Administrator account. Login to our account with our login id, and Windows will make the required settings. Just wait for a
|










Comments
Post a Comment